Talk about Slowloris and slow HTTP attacks
Slowloris is back?
Slowloris, a DDoS attack tool that has been around for at least a decade, has suddenly come back into the picture.
Microsoft suffered a DDoS attack in June this year that affected Azure, Outlook, OneDrive and some other businesses.
Finally, Microsoft officially disclosed the attack, the details can be referred to:
It is worth noting that this specifically mentions the means of attack including Slowloris:
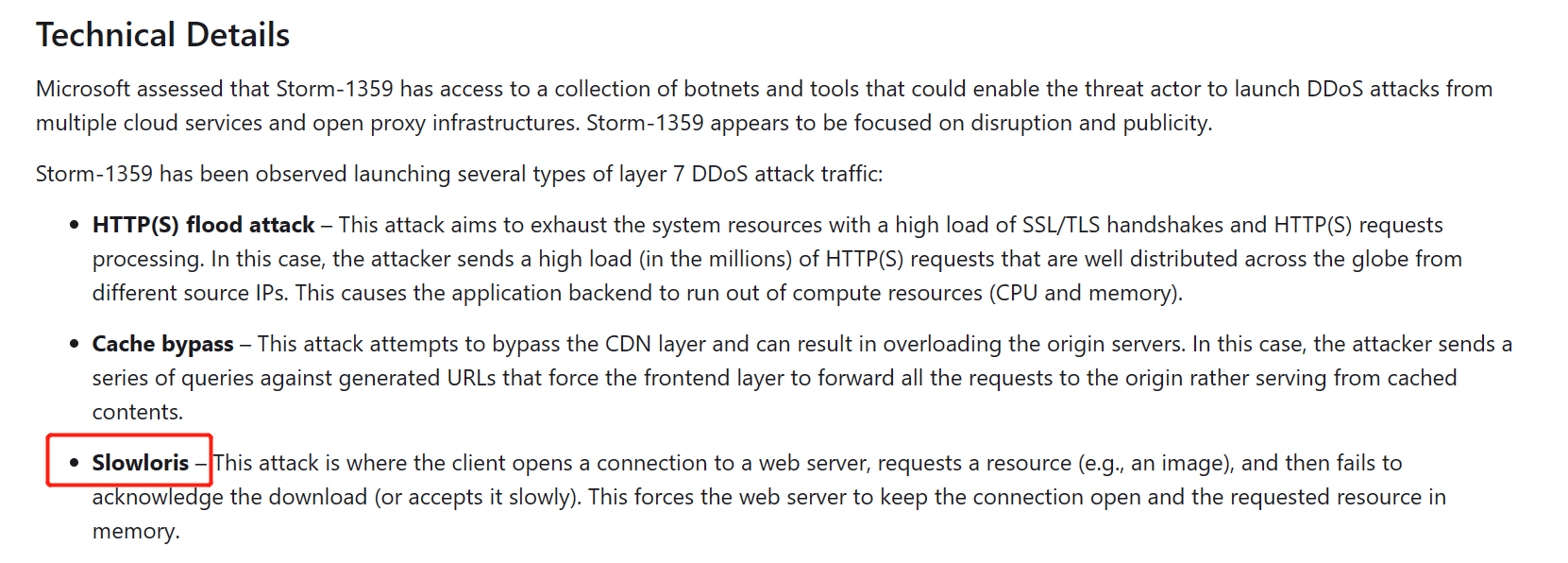
Slowloris history
Slowloris is a perl script, published in [http://ha.ckers.org/] (https://web.archive.org/web/20150426090206/http:/ha.ckers.org/) earliest. This website has shut down, you can take a look at < https://web.archive.org/web/20150426090206/http:/ha.ckers.org/slowloris >
There are now many rewritten versions available on github in various languages.
Slowloris was a very useful attack tool in that day, and make slow attack very famous.
The attack group Anonymous released a common attack toolkit in 2016, along with a dedicated demonstration video, which also featured Slowloris, making the tool more widely available to attackers.
Re-running the original version of Slowloris and seeing the logo pop up when it was running was full of memories.
When I discussed the principle and protection algorithm of this tool every day, and tested and verified the process, I was too friendly to see this logo.

Slowloris and slow HTTP attack principles and protection suggestions
now slow attack means have developed many kinds of attacks, kali has also integrated a variety of slow attack tools, you can use slowhttptest tool on it. At present, there are 4 attack tools integrated:
-H slow headers a.k.a. Slowloris (default)
-B slow body a.k.a R-U-Dead-Yet
-R range attack a.k.a Apache killer
-X slow read a.k.a Slow Read
Slow header
Attack principle:
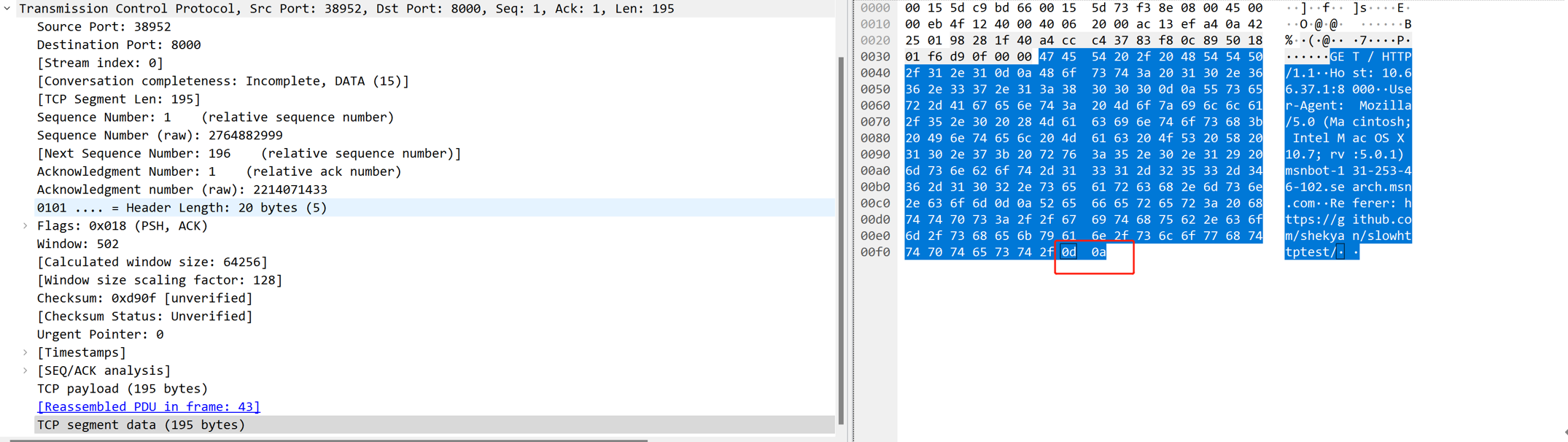
In normal HTTP Headers, it is end with two CLRF sections for HTTP headers. If the Web Server receives only one \r\n, it considers the HTTP Headers section unfinished and keeps the connection unreleased, waiting for the full request. The client then sends arbitrary HTTP headers to maintain the connection, which depletes the server thread pool and prevents the server from responding to denials of service.
This type of attack uses only a small amount of bandwidth, depleting server resources with very slow, normal-looking access rate requests while evading DDoS detection.
Example of normal http packets:
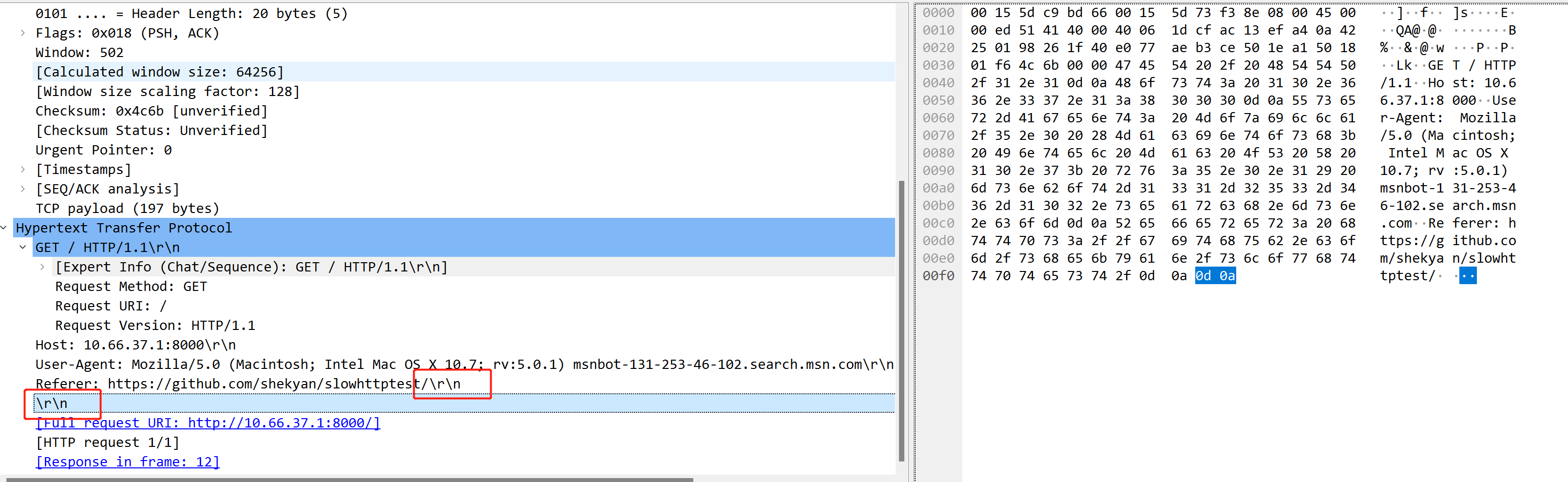
Attack message, only one \r\n:
Slow body
Attack principle:
In an http post packet, a large content-length is declared, but the body is sent slowly. As a result, the server is in the waiting state. As a result, the server resources are exhausted.
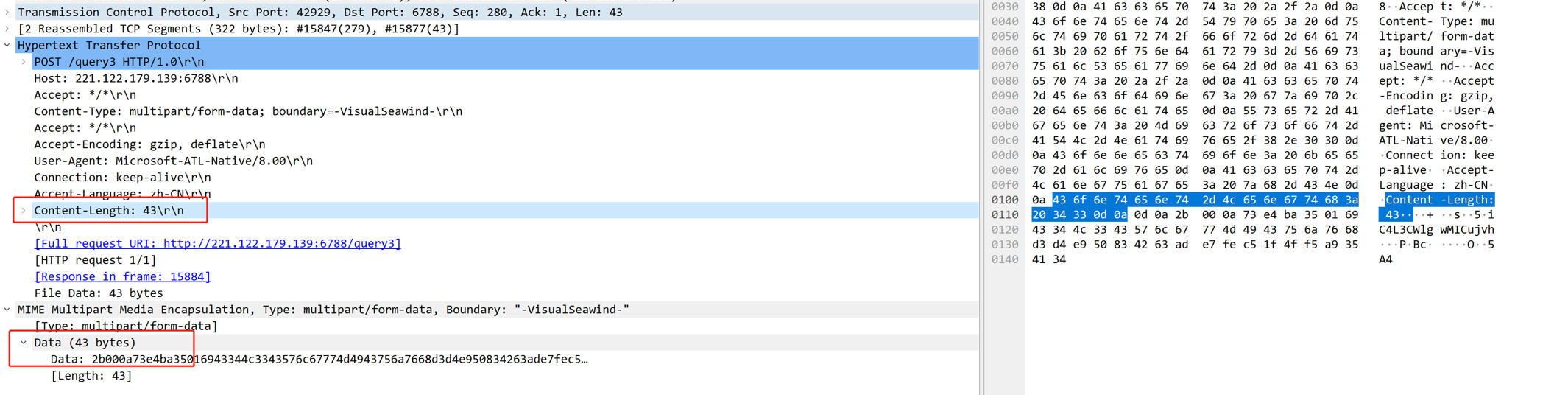
In normal packets, the content sent by a post is consistent with Content-length, for example, only 43 bytes are sent:
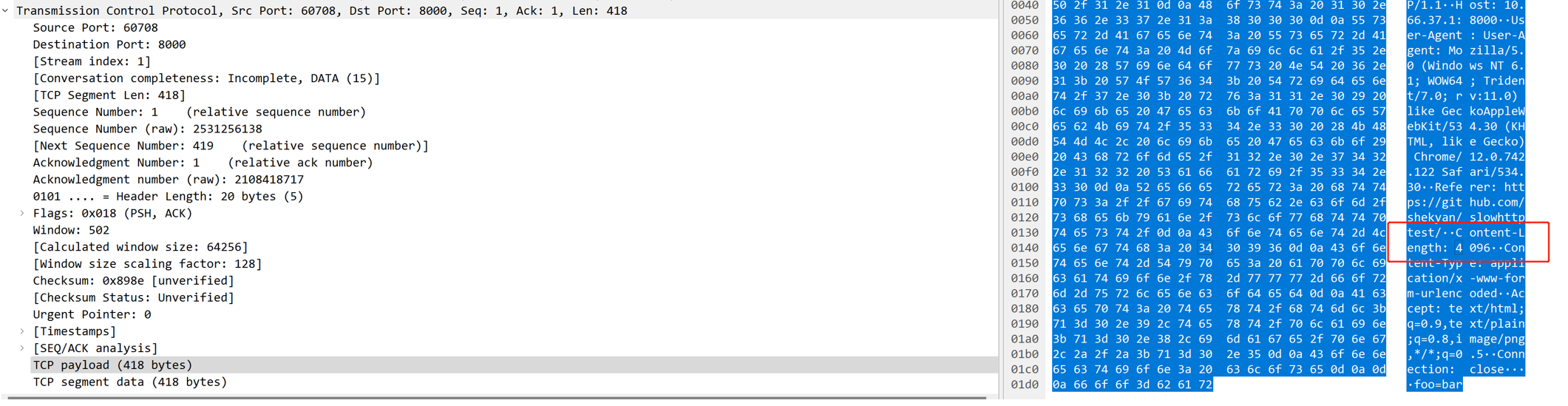
The Slow body attack declares 4096 bytes, but only sends more than 30 bytes slowly at a time:
Slow read
Attack principle:
In Slow read attack mode, a normal read request is sent to the server to request a large file, but the TCP sliding window is artificially small. The server then cuts the file to the size of the sliding window and sends it. Files remain in the memory for a long time, consuming resources.
TCP window Settings are smaller than the server’s socket cache, so data is sent slowly. At the same time, the requested file is larger than the socket cache of the server, so that the server cannot put the file into the cache at once, but must constantly cut the file into the window size and then put it into the cache.
The size of the normal TCP window is relatively large, and as the amount of data increases, the protocol supports the amplification ratio, which is generally very large:
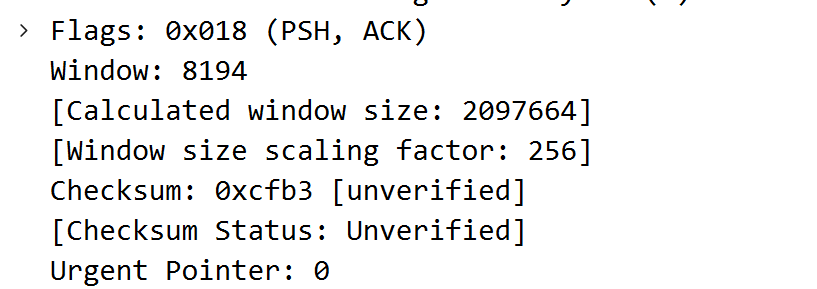
The TCP window size of the attack traffic is particularly small:
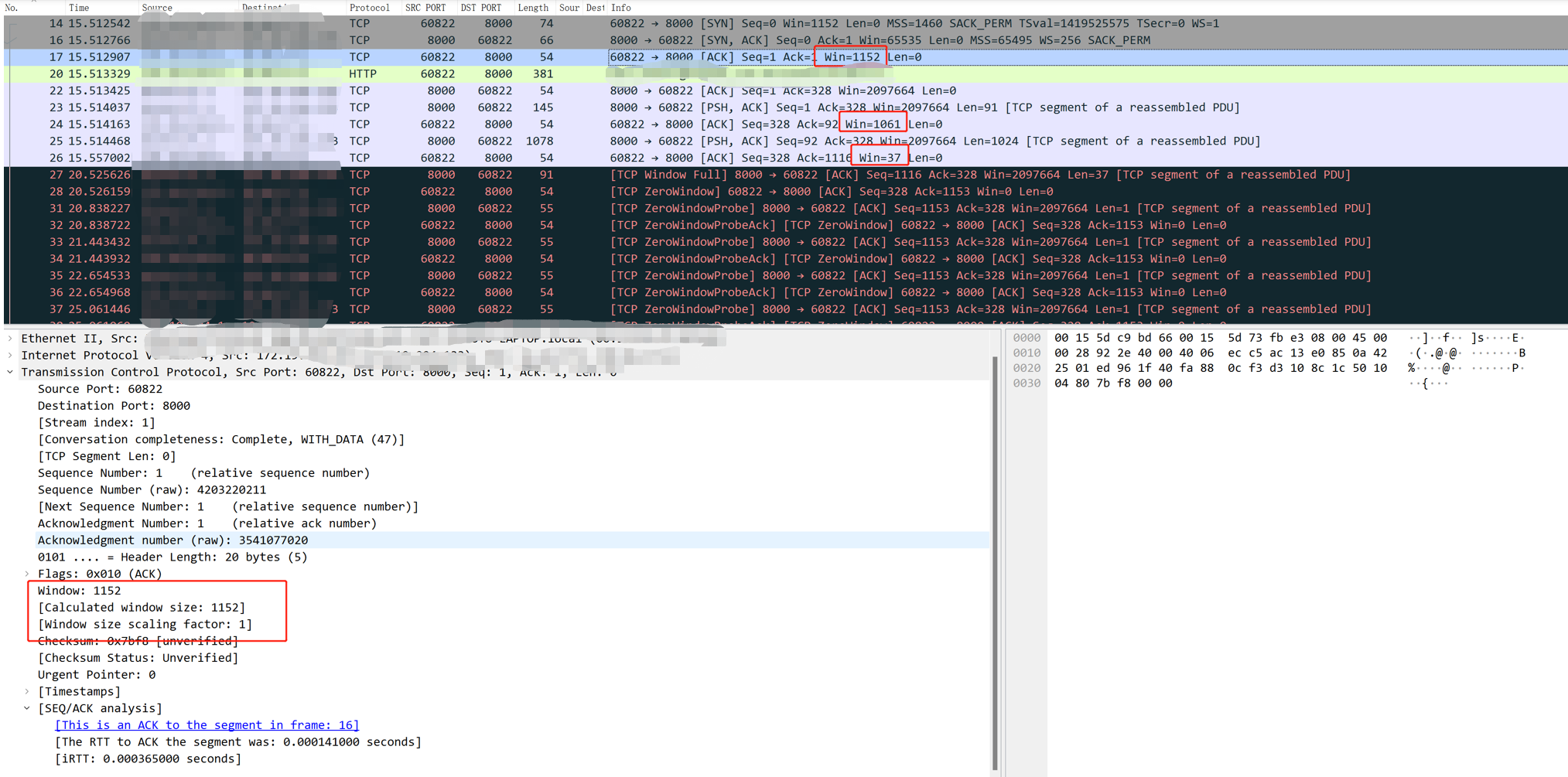
Range attack
Attack principle:
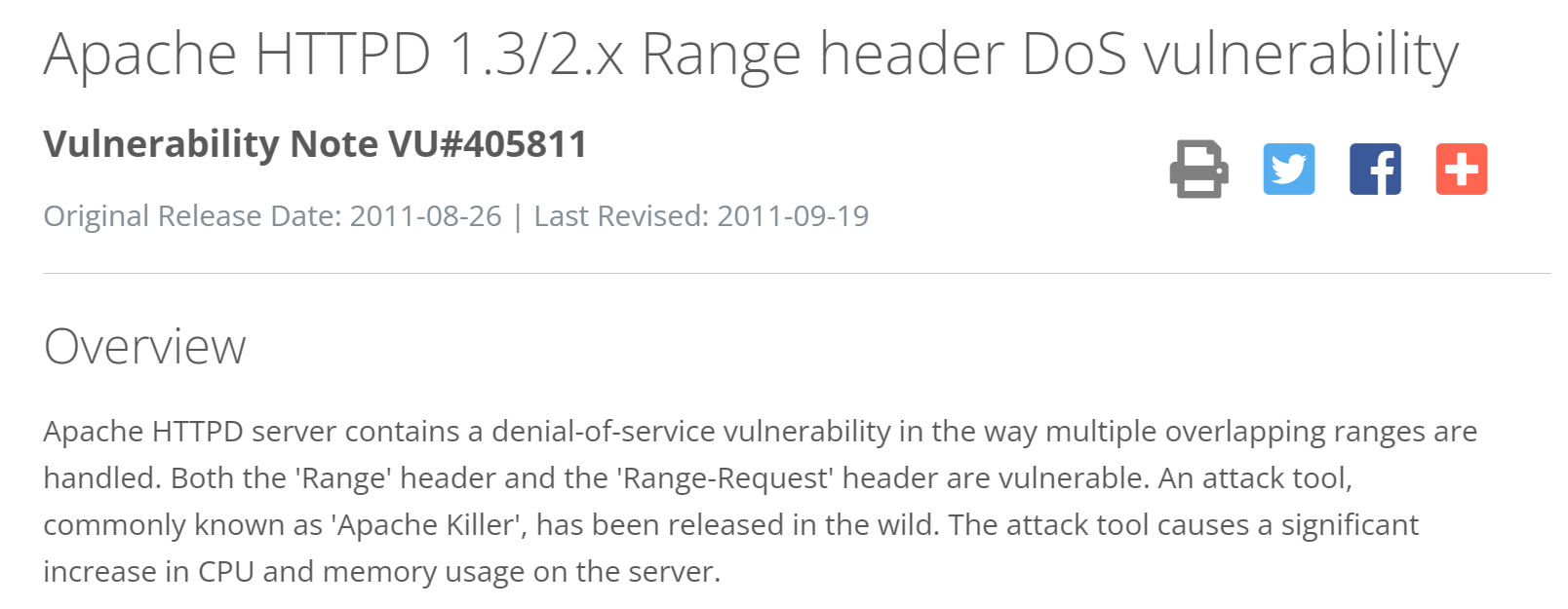
Range attacks can be regarded as DDoS attacks caused by vulnerabilities. Attacks take advantage of vulnerabilities on the Apache HTTPD server. A small number of requests may cause large memory and CPU usage on the server, affecting the normal services provided by the server. Vulnerability Details:
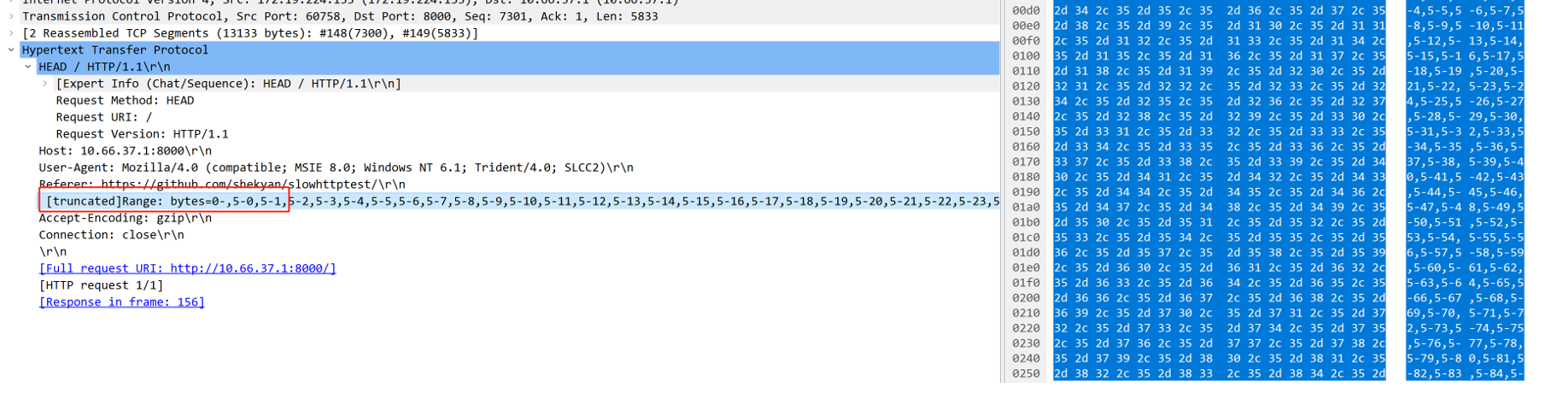
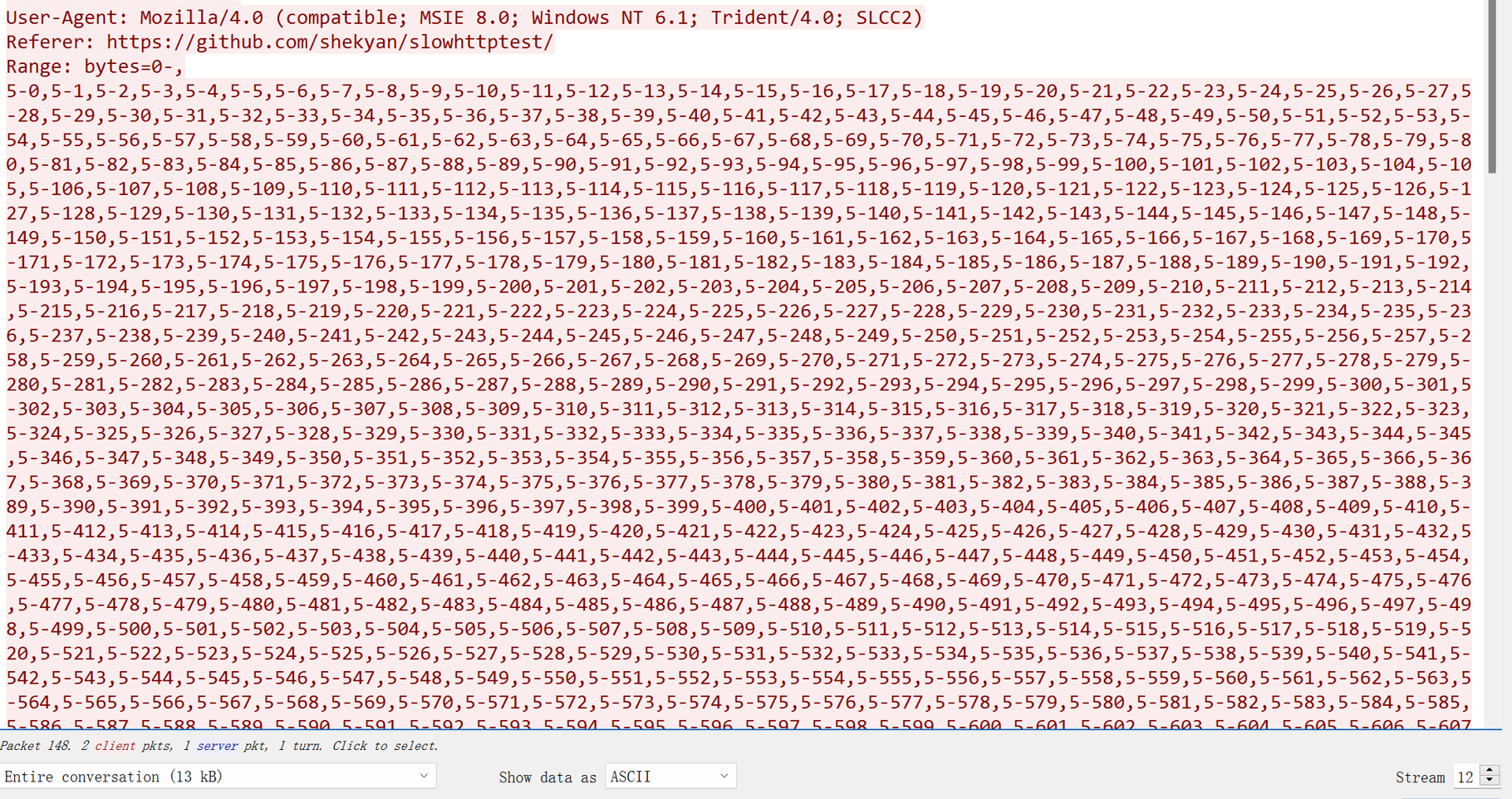
For example, the Range or Request-Range header is used in the attack packet:
Common protection methods
1、Increase server availability: Increasing the maximum number of clients allowed by the server at any one time increases the number of connections an attacker must make before the server becomes overloaded.
2、Limit the number of incoming requests: Limit the maximum number of connections allowed for a single IP address.
3、Cloud/security device-based protection: Protect the source server with a service that can act as a reverse proxy, buffering incoming requests before it starts sending anything to the source server.
4、Limit the maximum allowable time for HTTP Header transmission: If HTTP header transmission is not completed within the specified time, the source IP address is considered as a slow connection attack, and the connection is interrupted and added to the blacklist.
5、Configure an appropriate timeout period through the connectionTimeout attribute of the connector defined in server.xml.
6、check the size of content-length and window, and interrupt the connection and join the blacklist if it is abnormal.
At the end
The game of attack and defense is a permanent topic.
Although DDoS attacks are a time-honored and violent attack method, they are also constantly evolving, and new attack methods and tools often appear every once in a while.
Let’s finish with slowloris:
